Your Proven Security
Operations Partner
Build, manage, and maintain your Information Security Management
Program with Singular Security™
Be SingularReady.
At Singular Security we offer custom-tailored “cybersecurity-as-a-service” options that fit your business’s current needs, goals, and budget.
Continuous Monitoring & Threat Risk Mitigation
Singular Security™ offers 24×7 SOC Continuous Monitoring and Threat Hunting to secure your endpoints, networks, and cloud environments.
Through our managed or hybrid approach, we help your company with cost predictability, while maintaining visibility by offloading internal resources. Our security Analysts provide expert triage support, mitigating risks and responding to incidents in real time. With advanced Endpoint Security Services (EDR/XDR/MDR), we ensure seamless monitoring, rapid threat response, and ISM compliance.
![]()
Framework & Program Development
At Singular Security™, we design and maintain security frameworks aligned with NIST, tailored to your unique compliance needs.
We ensure your business is always a step ahead in defending against threats like phishing and ransomware. Our vCISO program provides you a clear roadmap for ongoing protection and offers Governance, Risk and Compliance Services Audit and Certification Support, Tabletop Exercises, IR Planning, Policies and Procedure Development.
![]()
Information, Security & Compliance Programs
Security and Corporate Compliance Awareness Training Programs for all employees and upper management foster a proactive security culture within your organization.
By equipping teams with essential knowledge, we help reduce the risk of phishing, ransomware, and other attacks, while preventing the mishandling of sensitive information within your company.
![]()
Emerging Trends: AI challenges & Data Protection
As businesses embrace cloud technology and remote work, new cybersecurity challenges arise.
Key solutions such as cloud security management, AI-driven threat detection, and Zero Trust security is essential for data protection. Singular Security™ offers tailored services and solutions, including cloud security and compliance management, ensuring your systems remain secure in a dynamic digital landscape.
Client Success
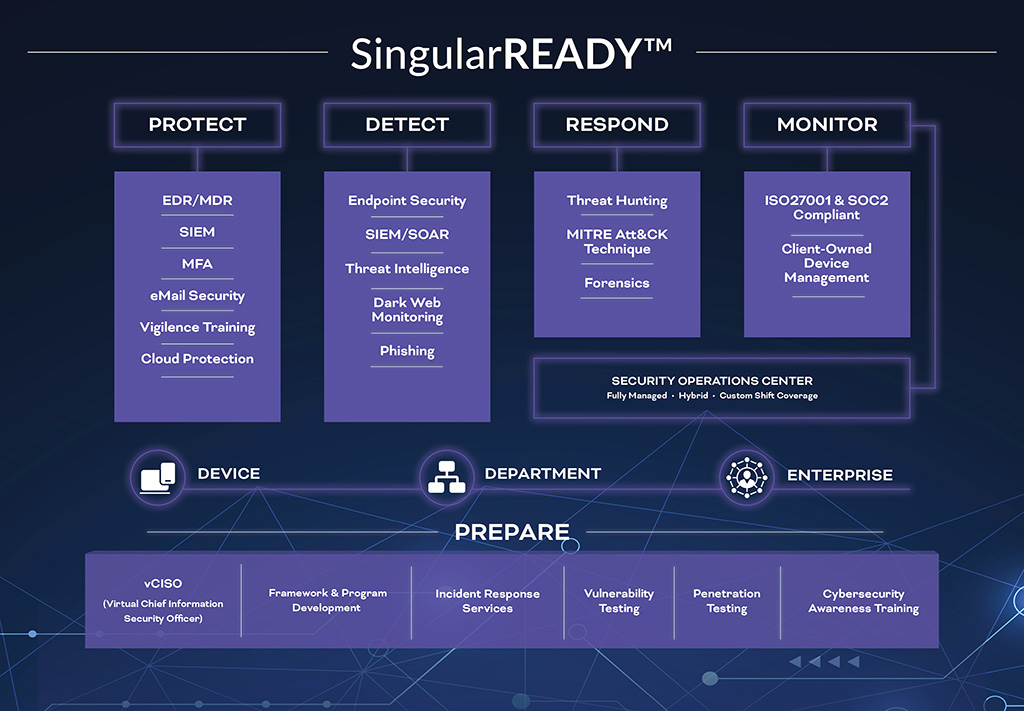
We understand that cybersecurity is not about paranoia. Its business value is in opening doors to contracts and projects through proving diligence and compliance that fits your company’s unique position in the market.
Cybersecurity is a process that requires a singular focus on awareness and readiness.
And it isn’t just about the ever-evolving threats to your information, hardware, and business. It’s about staying vigilant and compliant so you’re always ready for that next contract, that next project, that new direction your business needs to head.
