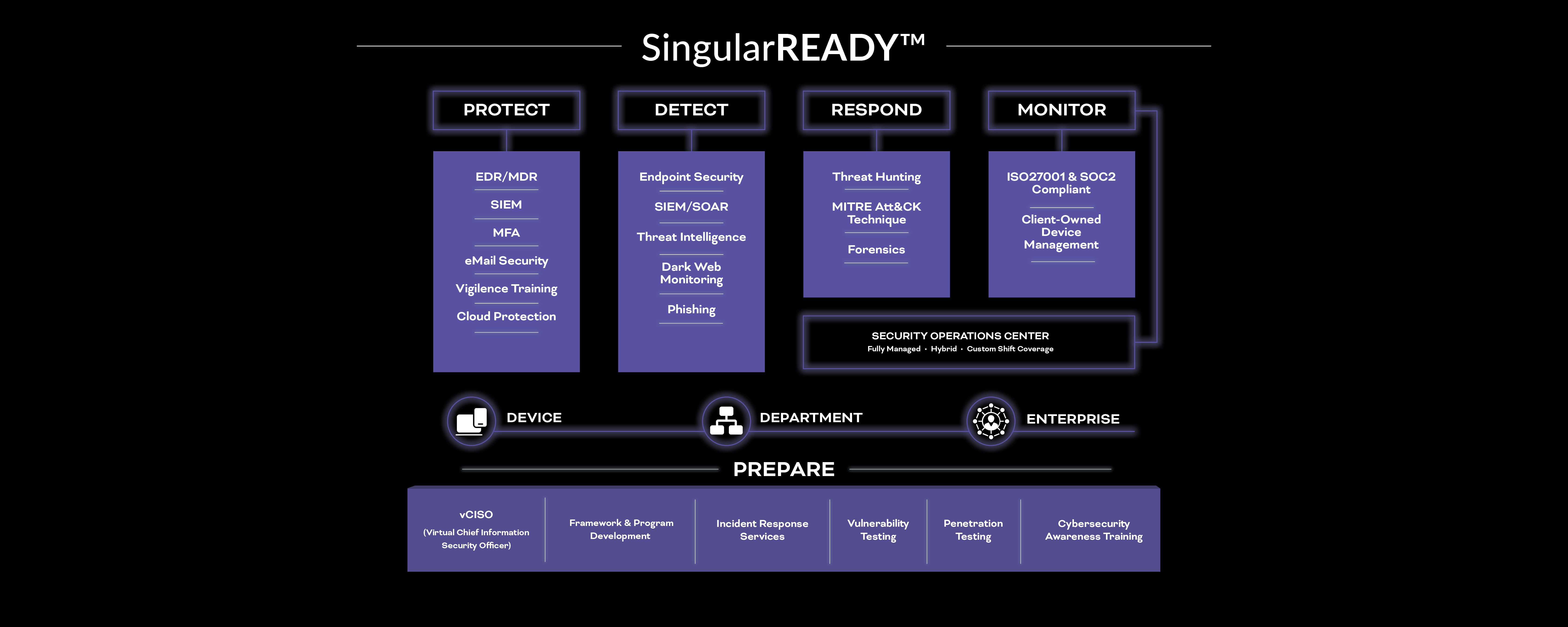
SingularREADY™
With SingularREADY™, you can build a security-first compliance program custom tailored to your unique businesses objectives that strengthens security, lowers risk, and passes audits.
Our flexible portfolio of solutions and services provides the people, processes, and technologies you need to establish, implement, and maintain a culture of security. With SingularREADY, you can implement and maintain vigilance using proven security, risk, and compliance solutions that resolve any gaps or deficiencies.
Gain visibility by integrating technologies
To protect your systems and networks, you need visibility across your complex environment. We work with you to hand-select tools that match your company’s industry, size, scale, business case, and regulatory compliance requirements.
With SingularREADY, you can build a security technology stack that includes:
- Application security scanning
- Database audit and monitoring
- Data loss prevention (DLP)
- Email Security
- Endpoint Detect and Response (EDR)
- Multifactor Authentication
- Patch Management
- Security awareness training
- Software inventory
- Vulnerability scanning
- Web Proxy & WAF Next Generation Firewall
Document to prove governance
A security-first approach to compliance means documenting all your activities. Our compliance experts understand your control requirements, working with you to identify and close gaps. We specialize in the mission-critical mandates that matter to your company’s industry, including:
- California Privacy Rights Act (CPRA)
- Center for Internet Security (CIS)
- Cybersecurity Maturity Model Certification (CMMC)
- Federal Information Security Management Act (FISMA)
- Federal Risk and Authorization Management Program (FedRAMP)
- General Data Protection Regulation (GDPR)
- Health Insurance Portability and Accountability Act (HIPAA)
- International Organization for Standardization (ISO) 27001
- National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171
- Statement on Standards for Attestation Engagements 18 (SSAE 18)
Partner with experts
Many companies struggle to comply with continuous monitoring and incident response requirements. To overcome the cybersecurity skills gap, we give you the security analysts and response staff you need through our Security Operations Center (SOC), Managed SIEM, and Vulnerability-Management-as-a-Service offerings.
With our services, you have the experts you need to:
- Analyze forensics
- Assess incident or crisis severity
- Correlate, analyze, and detect incidents
- Create incident reports
- Detect and remediate vulnerabilities
- Engage in threat hunting
- Incorporate behavioral analytics
- Leverage security analytics
- Monitor cloud services (Azure and AWS)
- Monitor threat intelligence
- Participate in weekly, monthly, and quarterly meetings
- Triage threats